티스토리 뷰
AWS certified cloud practitioner - Security, Migration and innovation , Variation Study
daylee de vel 2021. 6. 10. 17:19☁️ Security
Shared Responsibility Model
AWS Identity and Access Management (IAM)
AWS Compliance programs
AWS Artifact
AWS Artifact Follow Along
Amazon Inspector
AWS WAF
AWS Shield
Penetration Testing
Guard Duty
Key Management Service
Amazon Macie
Security Groups vs NACLs
AWS VPN
☁️ Migration and innovation
AWS Cloud Adoption Framework (AWS CAF)
☁️ Variation Study
Cloud* Service
Connect Service
Elastic Transcoder vs Media Convert
SNS vs SQS
Inspector vs Trusted Advisor
ALB vs NLB vs CLB
SNS vs SES
Artifact vs Inspector
☁️ Security
Shared Responsibility Model
IN: customer responsible in the cloud. OS, Firewall, Data misconfiguration, IAM
OF: AWS. H/W, Operation of Managed Services, Global Infrastructure
AWS Identity and Access Management (IAM)
- Create users to enable people and applications to interact with AWS services and resources
An IAM user is an identity that you create in AWS.
IAM policy is a document that allows or denies permissions to AWS services and resources.
An IAM role is an identity that you can assume to gain temporary access to permissions.
In IAM, multi-factor authentication (MFA) provides an extra layer of security for your AWS account.
AWS Compliance programs
When you first create an AWS account, you begin with an identity known as the root user.
compy with laws, rules, regulations
Data security standard
PCI: when you sell something online
AWS Artifact
- a service that provides on-demand access to AWS security and compliance reports and select online agreements.
purpose: if it's actually meeting a compliance?
access to AWS' security and compliance reports
Amazon Inspector
- AWS Inspector runs a security assessment and provides with a list of security findings
How do we prove an EC2 Instance is harden? (act of eliminating as many security risks as possible)
can perform both network and host assessments
popular benchmark is CIS which has 699 checks (center for internet security)
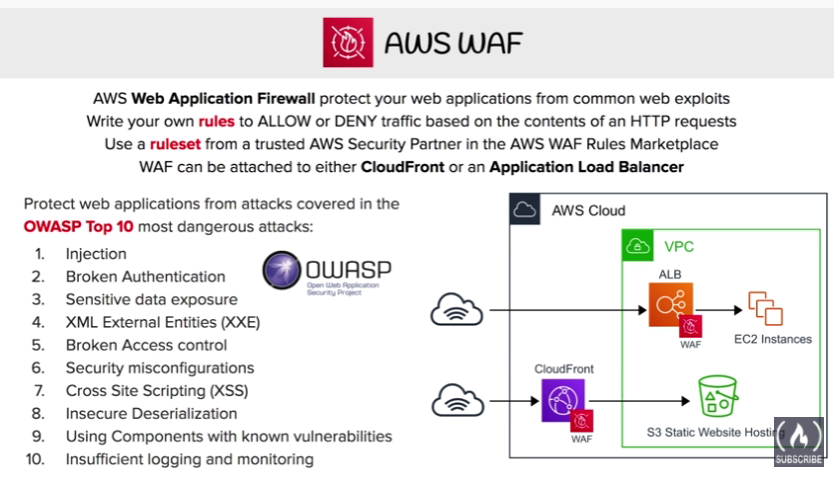
AWS WAF (Web Application Firewall)
- a web application firewall that lets you monitor network requests that come into your web applications.
protect from web exploits
can be attached to **CloudFront or Application Load Balancer**

AWS Shield
DDos (Distributed Denial of Service)
malicious attempt to disrupt normal traffic by flooding a large amount of fake traffic
all give automatic protections, at no additional charge
Route53 or CloudeFront you are using AWS Shield Standard
Protects you against Layer3(network),4(transport) and 7(app) attacks

Penetration Testing
simulated cyber attack on computer system to evaluate security, available on AWS
Guard Duty
- a service that provides intelligent threat detection for your AWS infrastructure and resources
IDS/IPS Intrusion Detection system, Intrusion Protection System
monitor unauthorized behavior. use ML to analyze AWS logs: CloudTrail logs, VPC Flow logs, DNS logs
it will alert you findings
Key Management Service (KMS)
- applications’ data is secure while in storage(encryption at rest)and while it is transmitted, known asencryption in transit.
encryption keys to encrypt your data
- multi-tenant HSM(hardware security module) for storing keys
- integrated to use KMS with a simple checknbox
- Envelope Encryption: protect your KEY by putting it in envelop

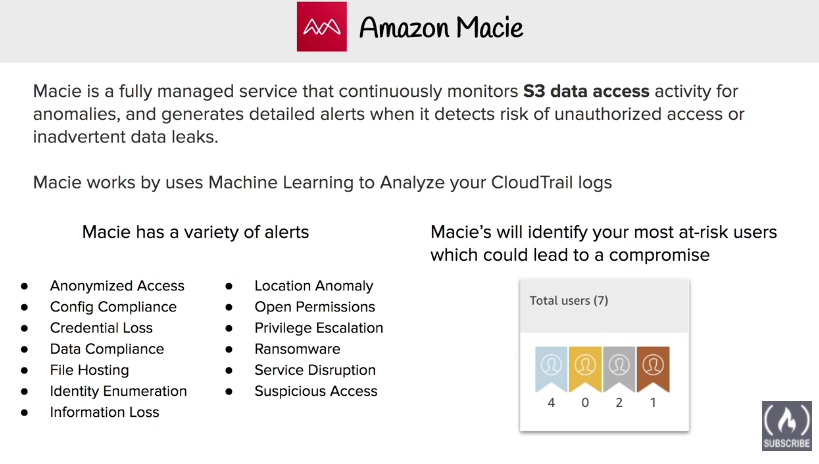
Amazon Macie
monitors S3 data access activities
Use ML to analyze your CloudTrail logs
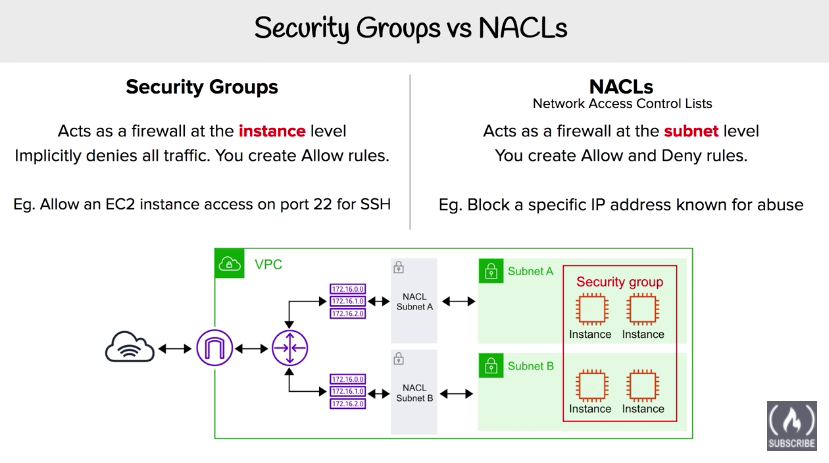
Security Groups vs NACLs (Network Access Control Lists)
both are firewalls
instance level(Allow rules) vs subnet level(Allow and Deny rules)
AWS VPN (Virtual Private Network)
lets you establish a secure and private tunnel

☁️ Migration and innovation
AWS Cloud Adoption Framework (AWS CAF)
6 Perspectives
- Business
to move from a model that separates business and IT strategies into a business model that integrates IT strategy. - People
helps Human Resources (HR) employees prepare their teams for cloud adoption by updating organizational processes and staff skills to include cloud-based competencies. - Governance
focuses on the skills and processes to align IT strategy with business strategy. This ensures that you maximize the business value and minimize risks. you understand how to update the staff skills and organizational processes that are necessary to ensure business governance in the cloud. - Platform
helps you design, implement, and optimize your AWS infrastructure based on your business goals and perspectives
also includes principles for implementing new solutions and migrating on-premises workloads to the cloud. - Security
- Operations
focuses on operating and recovering IT workloads to meet the requirements of your business stakeholders.
6 strategies for migration
- Rehosting
“lift-and-shift” involves moving applications without changes.
In the scenario of a large legacy migration, in which the company is looking to implement its migration and scale quickly to meet a business case, the majority of applications are rehosted. - Replatforming
“lift, tinker, and shift,” involves making a few cloud optimizations to realize a tangible benefit. Optimization is achieved without changing the core architecture of the application. - Refactoring/re-architecting
involves changing how an application is architected and developed, typically by using cloud-native features
(also known as re-architecting) involves reimagining how an application is architected and developed by using cloud-native features. Refactoring is driven by a strong business need to add features, scale, or performance that would otherwise be difficult to achieve in the application’s existing environment. - Repurchasing: moving to a different product
involves moving from a traditional license to a software-as-a-service model.
For example, a business might choose to implement the repurchasing strategy by migrating from a customer relationship management (CRM) system to Salesforce.com. - Retaining
might be deprecated
consists of keeping applications that are critical for the business in the source environment. This might include applications that require major refactoring before they can be migrated, or, work that can be postponed until a later time. - Retiring
the process of removing applications that are no longer needed.
AWS Snow Family
- AWS Snowcone is a small, rugged, and secure edge computing and data transfer device.
It features 2 CPUs, 4 GB of memory, and 8 TB of usable storage. - AWS SNOWBALL
- nowball Edge Storage Optimized
80TB HDD - Snowball Edge Compute Optimized
42TB HDD
- AWS SNOWMOBILE
You can transfer up to 100 petabytes of data per Snowmobile, a 45-foot long ruggedized shipping container, pulled by a semi trailer truck.
Machine Learning
- Amazon SageMaker, you can quickly and easily begin working on machine learning projects. You do not need to follow the traditional process of manually bringing together separate tools and workflows.
- Amazon Textract is a machine learning service that automatically extracts text and data from scanned documents.
- Amazon Lex is a service that enables you to build conversational interfaces using voice and text.
- AWS DeepRacer is an autonomous 1/18 scale race car that you can use to test reinforcement learning models.☁️ Variation Study
- Amazon Augmented AI (Amazon A2I) provides built-in human review workflows for common machine learning use cases, such as content moderation and text extraction from documents. With Amazon A2I, you can also create your own workflows for machine learning models built on Amazon SageMaker or any other tools.
The other response options are incorrect because:
Amazon Textract is a machine learning service that automatically extracts text and data from scanned documents.
Amazon Lex is a service that enables you to build conversational interfaces using voice and text.
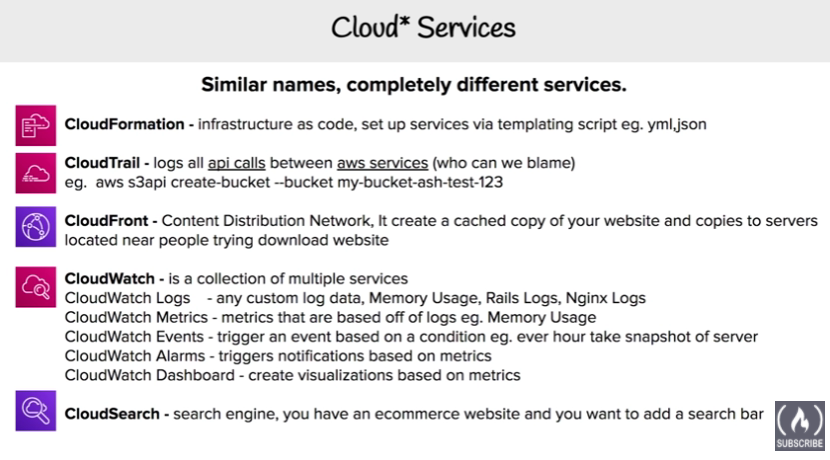
Cloud* Service
Connect Service

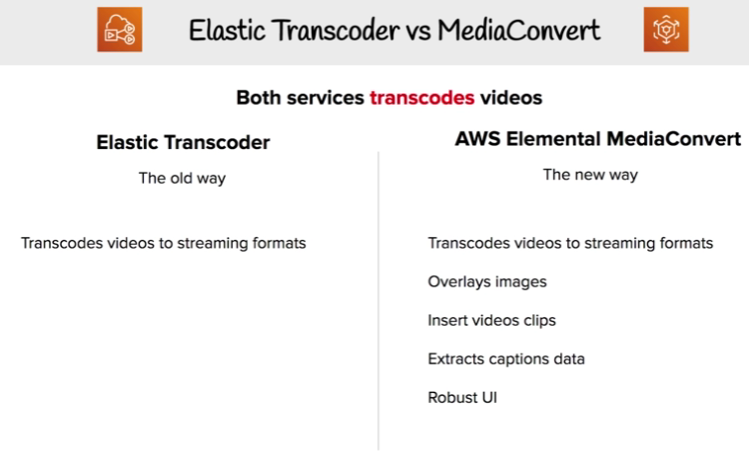
Elastic Transcoder vs Media Convert
SNS vs SQS
tightly coupled architecture can fail when single compenents have failure. More realiable, Loosely coupled architecture, won't cause cascading failures
*Amazon Simple Notification Service (Amazon SNS): can send out end users. subscribers of topics == web servers, email addresses, Lambda functions etc *
*Amazon Simple Queue Service (Amazon SQS): msg queueing service. send store receive msgs. msgs place until they delivered * between distributed application components. Which service should you use

SNS vs SES

Inspector vs Trusted Advisor

ALB vs NLB vs CLB ( Load Balancer)

Artifact vs Inspector

'CS > Web' 카테고리의 다른 글
| Port (0) | 2021.06.20 |
|---|---|
| AWS training - essentials index (0) | 2021.06.15 |
| 비전공자 개발자 AWS Cloud Practitioner 합격 후기 공부 계획 팁 유튜브 덤프 (0) | 2021.06.09 |
| AWS certified cloud practitioner - Technology Overview: Networking, Database (0) | 2021.06.09 |
| AWS certified cloud practitioner - EC2 Pricing Models, Billing and Pricing (0) | 2021.06.08 |
